
What's the deal with encryption strength —is 128 bit encryption enough or do you need more? | by Lance Gutteridge | Medium
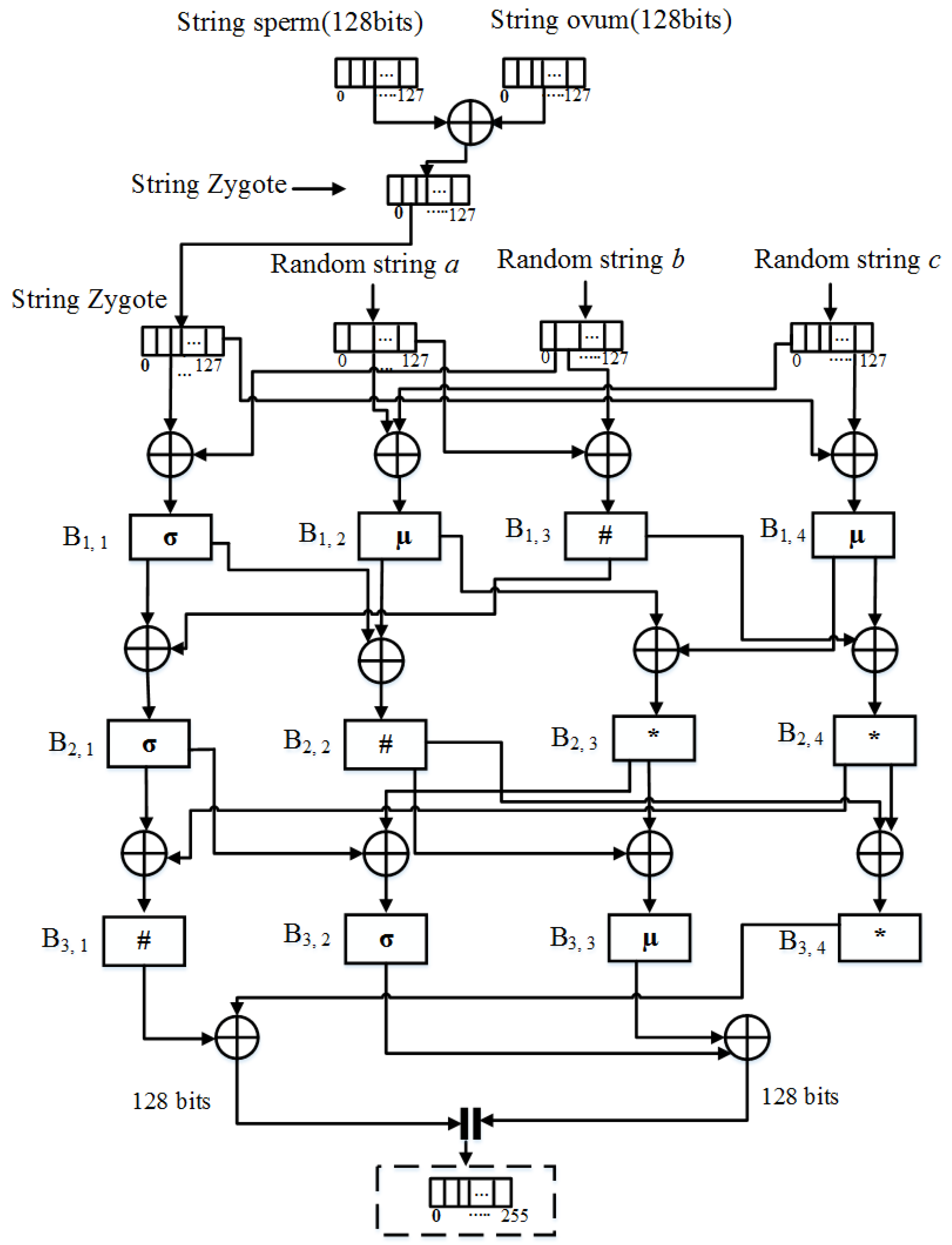
Applied Sciences | Free Full-Text | Omega Network Pseudorandom Key Generation Based on DNA Cryptography

An example of a 36-character string depicting a 128-bit binary value in... | Download Scientific Diagram
GitHub - joe-darkmatter/node-red-contrib-aes-128-cbc: A hex string-based 128 -bit AES with specifically CBC mode of operation ciphering algorithm for Node-Red module









![java - String vs char[] - Stack Overflow java - String vs char[] - Stack Overflow](https://i.stack.imgur.com/WhEBr.png)